Introduction to Malware Analysis
- Introduction to Malware Analysis
- Preliminary Analysis Techniques
- Environment for Malware Analysis
- Static Malware Analysis
- Dynamic Malware Analysis
- Understanding Malware Behaviour
- Reverse Engineering
- Advanced Static Analysis
- Advanced Dynamic Analysis
- Anti-Reverse Engineering
- Malware Attribution
- Malware Mitigation and Prevention
Static Malware Analysis
Disassembling Programs: A Comprehensive Guide
Any low-level programming language in which there is a very strong correspondence between the instructions in the language and the architecture's machine code instructions.
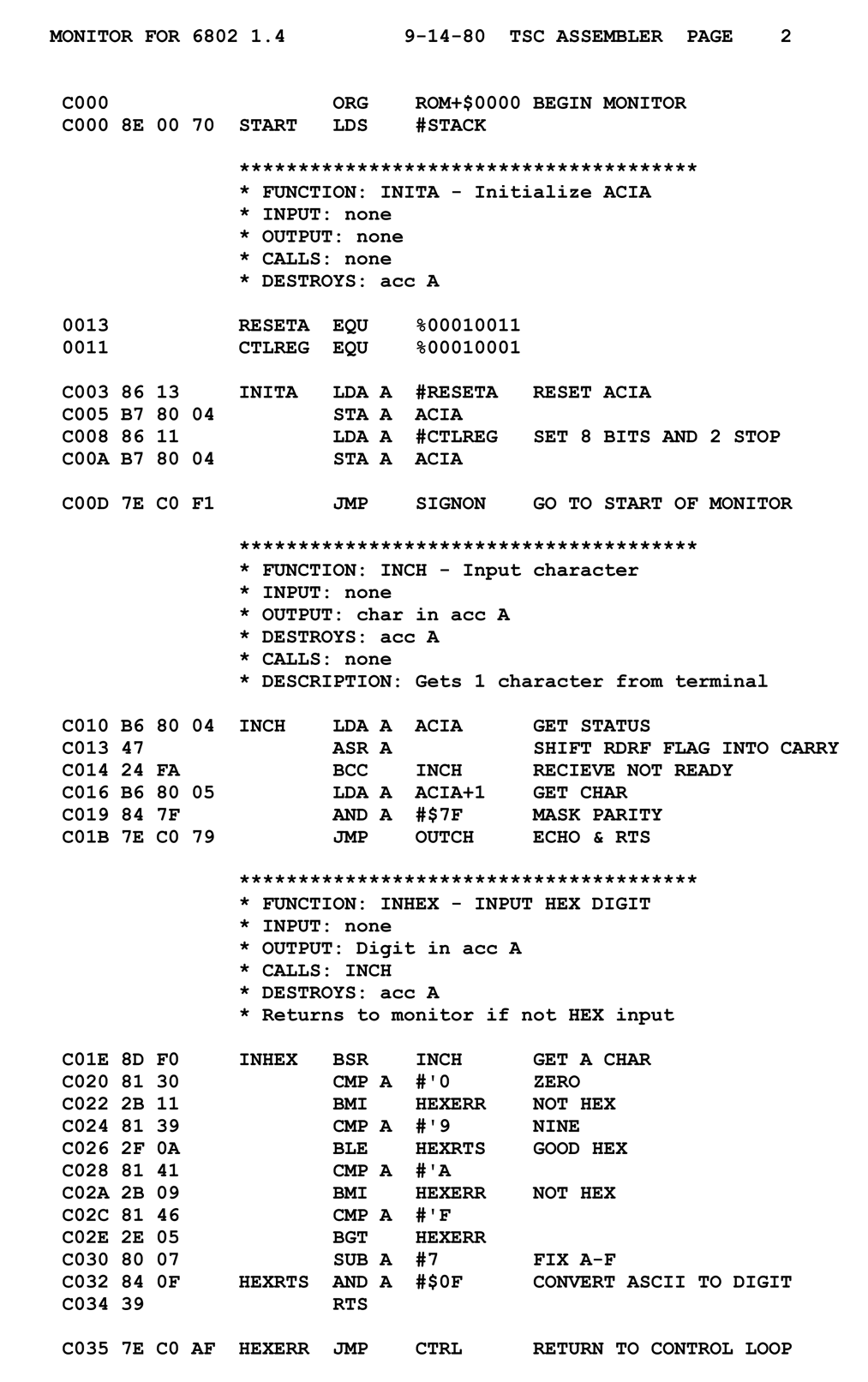
Disassembling programs is a crucial part of static malware analysis. It involves translating the binary instructions of a program into assembly language. This process allows analysts to understand the program's functionality without executing it, which is particularly useful when dealing with potentially harmful malware.
Introduction to Disassemblers
Disassemblers are tools that translate machine language into assembly language. They are essential for malware analysts as they allow them to understand the inner workings of a program without the risk of executing potentially harmful code.
There are several disassemblers available, each with its own strengths and weaknesses. Two of the most popular are IDA Pro and Ghidra.
Understanding Assembly Language Basics
Assembly language is a low-level programming language that is specific to a particular computer architecture. It is one step away from machine code, the binary instructions that a computer's hardware executes.
Understanding assembly language is crucial for malware analysis. It allows analysts to understand what a program does by reading its code, even if the source code is not available.
Here are some basic assembly language concepts:
- Registers: These are small storage areas where the CPU stores data it needs to access quickly.
- Instructions: These are the commands that the CPU executes. They can perform operations like moving data, performing arithmetic, or controlling the flow of the program.
- Operands: These are the values that instructions operate on. They can be constants, registers, or memory addresses.
Using Disassemblers: IDA Pro and Ghidra
IDA Pro and Ghidra are two of the most popular disassemblers used in malware analysis.
IDA Pro is a commercial product known for its extensive features and support for a wide range of architectures. It offers both a disassembler and a debugger, making it a versatile tool for malware analysis.
Ghidra is a free, open-source software reverse engineering (SRE) suite developed by the National Security Agency (NSA). It includes a disassembler among its many tools. Ghidra's codebase is publicly available, which allows users to modify and improve the tool.
Both IDA Pro and Ghidra provide graphical interfaces that make it easier to navigate and understand the disassembled code. They also offer features like function identification, cross-referencing, and annotation, which can help analysts understand the program's structure and functionality.
Identifying Malicious Code Patterns
Once a program is disassembled, the analyst can start looking for patterns that suggest malicious activity. These can include:
- Code obfuscation: Malware authors often use techniques like encryption, packing, or garbage code insertion to make their code harder to analyze.
- Suspicious API calls: Certain Windows API calls are commonly used by malware, such as those that open network connections, modify files, or manipulate processes.
- Control flow anomalies: Malware often exhibits unusual control flow, such as loops that run for an unusually large number of iterations or conditional branches based on seemingly random conditions.
By understanding these patterns, analysts can identify potentially harmful code and gain insights into its functionality. This knowledge is crucial for developing effective countermeasures and mitigating the threat posed by the malware.